The analytics engine built for Higher Education. Now available to strategic leaders in any sector.
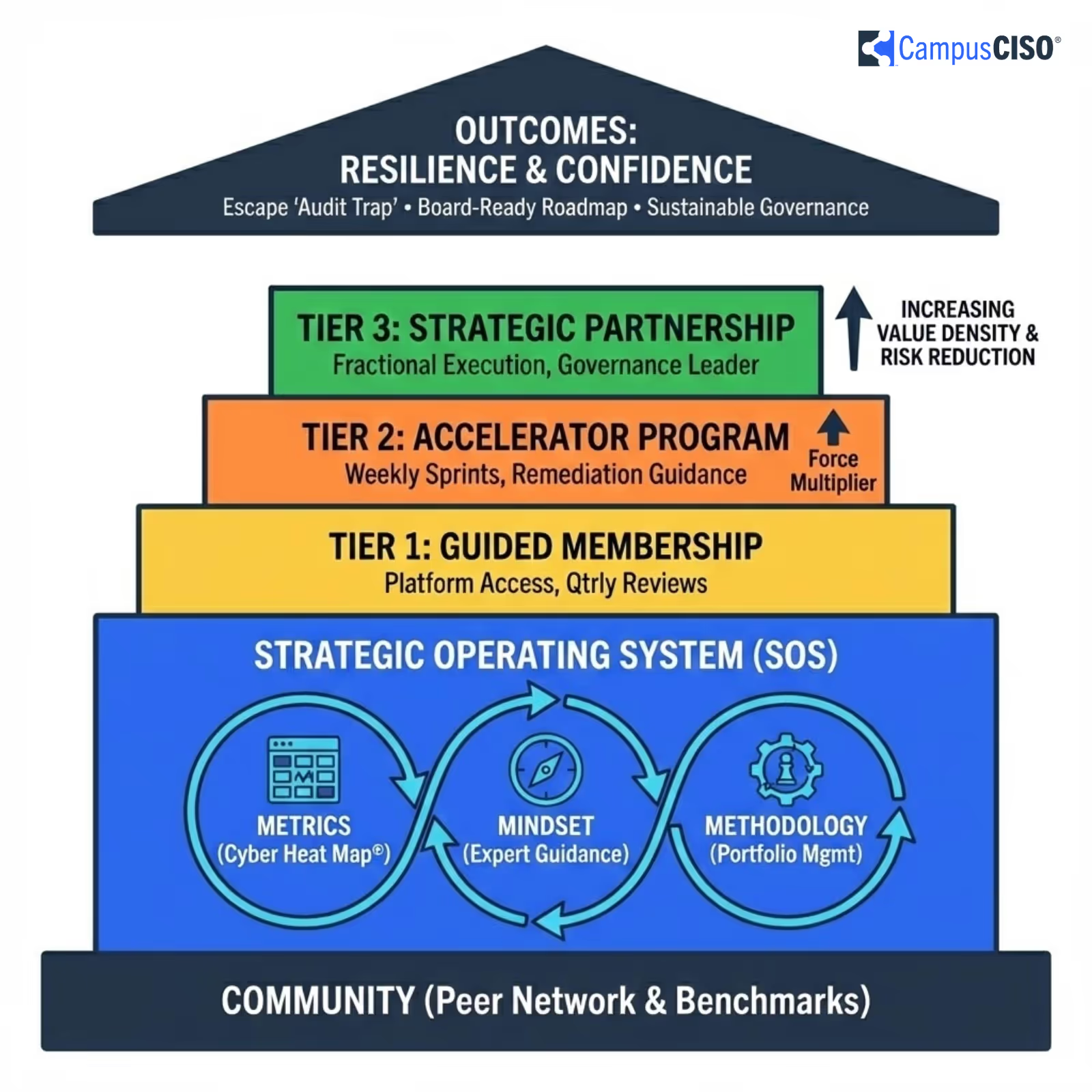
You already have audits and tools. What you need is a living, defensible plan, prioritized using your data and relative cost and effort, with updates in days, not months.
Cyber Heat Map turns scattered inputs into one plan you can maintain and explain.

Complete Your Cybersecurity Roadmap in 30 Days
30‑Day Cyber Diagnostic - $399
Founder‑led kickoff, 30 days of platform access, and weekly group guidance.
No long-term commitment.
Just results.
Reserve Your Seat via CampusCISO
Ready to get started? Purchases are handled through CampusCISO. If you're a consulting firm, you can request a partner pilot.


Collecting findings is not enough. What matters is a ranked list of next moves you can fund this quarter, plus friendly guidance to keep momentum.
Founder‑led kickoff and weekly strategy sessions help you finish fast, interpret results, and finalize your plan.
Complete your baseline in hours and update in minutes. Keep one living plan across people, process, and technology, prioritized with real‑world data and peer benchmarks.
A private, vendor‑neutral space for practical exchange with other leaders. Learn what works, share templates, and stay aligned.
A one‑page view that ranks your next investments, with relative cost, effort, and plain‑English rationale.
Refresh in minutes when conditions change, so updates are routine, not a heavy lift.
Defend funding with data and peer context, not opinions or binders of static plans.

Over 140 leaders have used Cyber Heat Map to produce data‑informed, board‑ready plans quickly. Here is what they say:
Build a data‑informed, board‑ready roadmap in 30 days, then keep one living plan aligned to your goals.

