
Cyber Heat Map turns cybersecurity assessment data into a clear, executive-ready roadmap. Its “sand in a box” model shows leaders where foundational gaps limit higher-level maturity, then ranks each potential project. The result is a data-driven plan that helps budget-constrained schools, municipalities, and mid-sized companies strengthen security one layer at a time, supported by benchmarks and continuously updated guidance.
Cyber Heat Map helps IT and security leaders turn cybersecurity assessment data into an actionable roadmap and executive reports. In less than a day, you can:
Organizations often invest in advanced cybersecurity tools but neglect basic security practices. This is like adding a high-tech alarm system to a house while leaving your doors unlocked and windows open.
We got our start helping college and university CIOs as they reviewed and planned their cybersecurity strategies. Cyberattacks pose a major threat to education. A recent EDUCAUSE article reveals schools face 2,300 cyberattacks every week. However, colleges and universities are still under-resourcing their cybersecurity tools and personnel.
With flat budgets, thousands of vendors vying for attention, and constant threats, leaders need tools that help them prioritize funding. We designed Cyber Heat Map to help busy technology executives do that more efficiently.
We knew many organizations could benefit from an affordable and pragmatic cybersecurity planning platform, so we developed the Cybersecurity Higher Education Assessment Tool Strategy Map (Cyber H.E.A.T. Map).
This was initially just a (very large) spreadsheet that we used with clients to help identify security weaknesses and develop practical improvement roadmaps. It proved valuable in pinpointing gaps and guiding leaders as they shaped their strategies. As demand grew, we evolved from a standalone spreadsheet to an online assessment and planning tool.
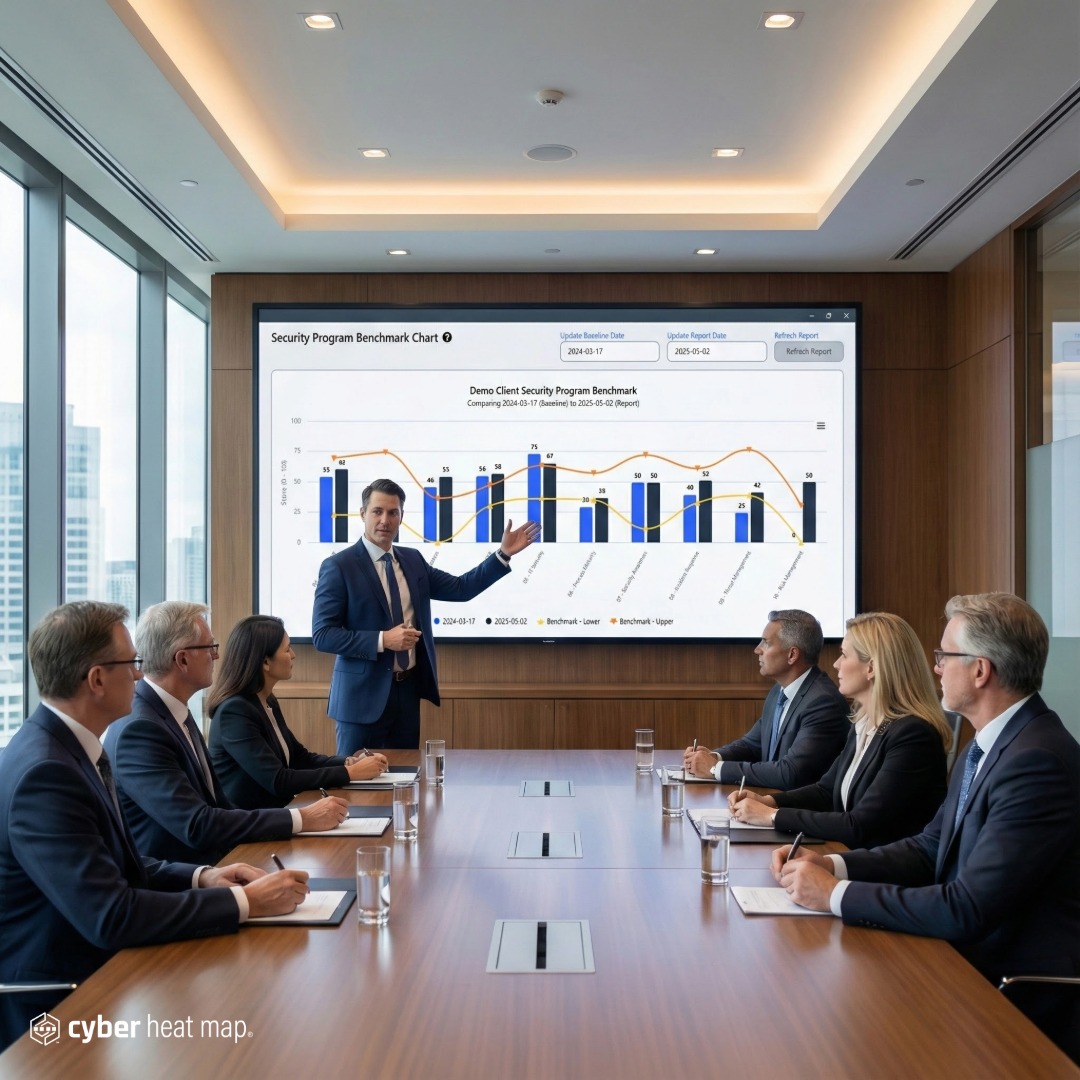
Notice our website lacks prominent examples of a traditional “heat map” report, despite the product name. This is deliberate. While the framework’s data enables strategic leaders to create heat maps for their teams, its true value comes from how Cyber Heat Map helps prioritize potential cybersecurity improvements. Consider a generated heat map report as a small part of a larger system. It’s supported by a structured methodology that guides technology leaders as they address immediate threats and build lasting improvements.
We tailored the assessment methodology to help organizations with limited resources by focusing on the most impactful 20% of activities (the Pareto principle). We reduced the time teams spend on low-value tasks and prioritized activities that led to actionable recommendations. This shifted the effort from lengthy checklists to practical evaluations of cybersecurity technology and personnel.
Over time, Cyber Heat Map evolved into an online platform that simplifies cybersecurity investment decisions. We wanted to give leaders more time for strategic planning instead of routine administrative tasks. Its early success with higher education clients led to requests to support other sectors. With our May 2025 relaunch, any organization can use this planning engine alongside schools and colleges. What do our typical customers have in common? They need practical, budget-conscious cybersecurity guidance.
The Cyber Heat Map framework approaches how organizations prioritize security investments using a powerful visual metaphor: the “sand in a box” principle. Imagine your cybersecurity program as a box, divided horizontally into domains and vertically into maturity levels. Now picture your security investments are like grains of sand. Pouring resources (sand) into the box shows how they distribute and spread out before building up.
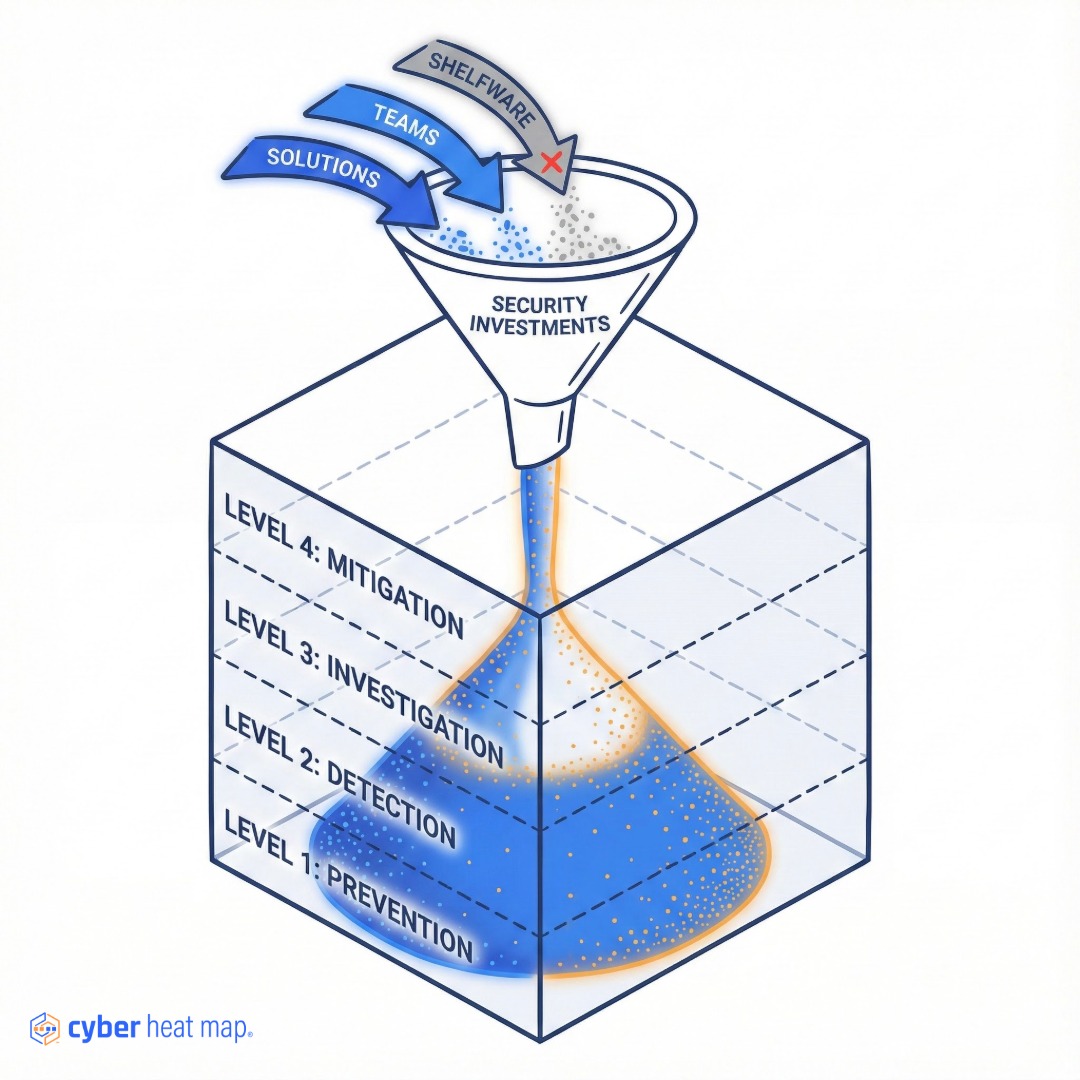
Cybersecurity investments should follow a similar construct: build a strong foundation across all technical areas before tackling advanced capabilities.
Traditional security assessments often treat each framework and control in isolation, ignoring dependencies between capabilities and implementation order. However, real-world security is interconnected. Advanced capabilities, such as threat hunting, require a solid technical foundation. Without basic capabilities like asset management and network segmentation in place, even sophisticated AI-enabled tools underperform.
Imagine pouring sand into the box again. Piling sand high in one spot without expanding to build a solid base makes the whole thing collapse. Similarly, neglecting cybersecurity fundamentals, like a thorough asset inventory, before investing in advanced tools like XDR creates instability, wastes resources, and leaves dangerous vulnerabilities. Leaders need to prioritize building a strong foundation.
Cyber Heat Map clarifies the complex vendor landscape. We give insights to help busy IT leaders strengthen their security capabilities with a practical approach that gives them confidence their existing infrastructure will support new investments.
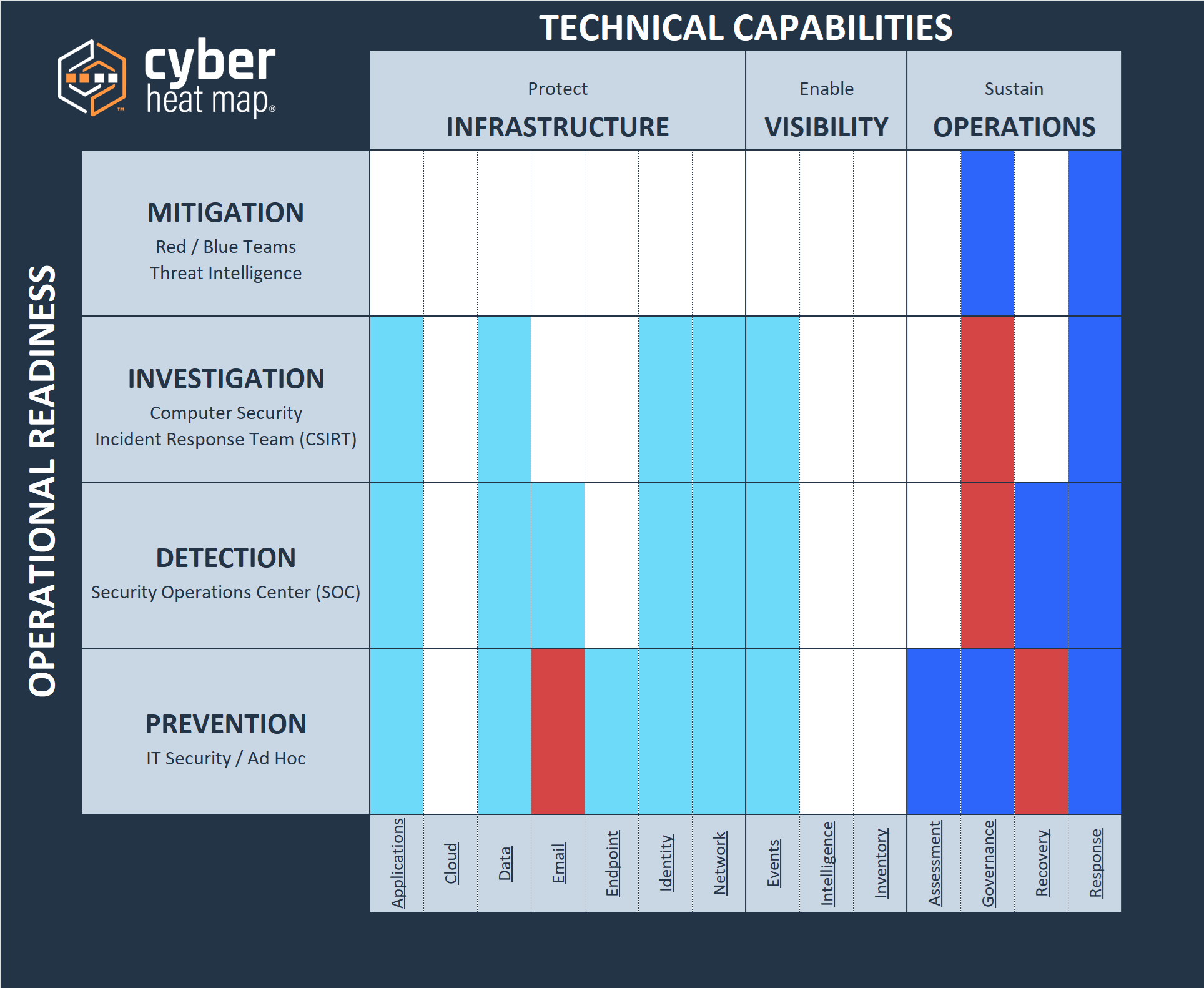
To apply the “sand in a box” principle, Cyber Heat Map uses a matrix structure that clarifies the complex cybersecurity landscape. The horizontal axis divides cybersecurity into 14 technical domains, grouped under three broad functions:
The vertical axis organizes capabilities into four progressive maturity stages:
Cyber Heat Map maps each capability to a technical domain and one or more maturity levels. This structure helps us instantly highlight strengths, weaknesses, and imbalances. For example, strong Network Prevention and Investigation (firewalls, access control) might contrast with a gap in Detection (missing intrusion prevention or network sandboxing). This gap could hinder the effectiveness of your more advanced tools.
While the online Cyber Heat Map application does not include a traditional “heat map” report, we provide a template that strategic leaders can use to turn their assessment data into a more traditional heat map.
Leaders can easily see their cybersecurity investments in context. New projects should fill lower-level gaps before tackling higher ones. This structured approach clarifies the chaotic cybersecurity market, transforming confusing point solutions into a clear capabilities map. For example, you can easily see if they purchased advanced email mitigation tools while lacking more foundational email security capabilities, such as Email DMARC authentication.
The matrix shows how Cyber Heat Map builds your personalized recommendations from the assessment data, even if the actual calculations are hidden. Cyber Heat Map is more than paperwork. It’s a practical, strategic blueprint for cybersecurity improvement.
The practical value of Cyber Heat Map is best seen through actual examples.
Instead of generic advice, it prioritizes recommendations based on your organization’s assessment data. It considers factors like whether the capability supports compliance and risk mitigation goals, whether you already own solutions, and whether you have staff who can support the project. This data-driven approach often reveals surprising insights, challenging many common planning assumptions about cybersecurity.
For example, one college’s Cyber Heat Map assessment prioritized implementing Email DMARC authentication. At the time, higher education did not widely deploy DMARC. Many institutions ignored it since email providers hadn’t mandated compliance.
Why was DMARC a top recommendation for this college?
Several factors contributed to its high priority score: they already owned the necessary email security tools, they had staff with the skills to configure DMARC, and this capability would address a known weakness by protecting against spoofed emails and phishing. The analysis revealed a high-impact, low-effort opportunity. By assigning a high priority score, Cyber Heat Map helped the CIO recognize a critical security improvement that was well within reach.
The team implemented DMARC over several months. Soon after finishing, Gmail and Yahoo tightened DMARC enforcement by rejecting or flagging non-compliant messages. Because they had already implemented DMARC based on Cyber Heat Map recommendations, the college was prepared months ahead of the change by email providers.
Organizations using Cyber Heat Map often find their assumptions challenged. A CIO might believe a new Zero Trust solution or an AI-powered SOC tool are most important based on marketing they have read. The recommendations report in Cyber Heat Map might help them understand how improving asset inventory or implementing risk-based multi-factor authentication is more critical for their specific needs.
Cyber Heat Map’s data-driven analysis provides objective recommendations based on technical dependencies, resource availability, risk reduction, and compliance. The result is a practical roadmap that confirms some intuitions while revealing unexpected insights.
In addition to deploying the right technology, strong cybersecurity requires a plan that incorporates people, processes, and preparedness. The Cyber Heat Map cybersecurity capability assessment gathers data across five key areas:
Modern cybersecurity products often include unused features. This assessment addresses this by separating tool ownership from capability implementation, revealing potential shelfware and underutilized functionalities. It clarifies the difference between your existing tools and the capabilities you actually employ.
Understanding staff skills and process maturity reveals opportunities to use existing strengths and address weaknesses. For example, you might find an employee with valuable cloud security expertise or a need for team-wide incident response training. This blend of technology and human insights is crucial, particularly in organizations with staffing shortages are prevalent.
Cyber Heat Map helps organizations maximize impact by aligning training and outsourcing with their technology and skills inventory. Schools and smaller organizations often find existing resources—people and tools—sufficient before investing in new solutions or staff.
Cybersecurity success relies on people, processes, and technology, and Cyber Heat Map helps strengthen all three.
We help leaders balance their immediate needs and long-term goals, even with lean or decreasing budgets. The platform automates many activities so busy security teams can focus on their core jobs instead of filling out spreadsheets.
This approach helps leaders understand their gaps and shape long-term plans. Cyber Heat Map helps leaders strike this balance. It flags urgent issues while showing a path toward building long-term defenses.
Although we’ve tried to keep the planning platform very easy to use and understand, Cyber Heat Map’s effectiveness hinges on avoiding some common mistakes.
The framework delivers maximum value when the leaders who own cybersecurity budgets and strategy are involved in the assessment, along with the technical experts who operate the tools.
Even with a single-user Cyber Heat Map license, we recommend gathering key stakeholders, including the CIO, CISO, security architects, and IT managers, in one room to complete the initial assessment collaboratively. This can often be finished in a single afternoon.
When organizations delegate the assessment to a junior analyst working in isolation, we frequently see the process take longer than it should, with incomplete data and missed insights. The process is fastest and the results are most accurate when leadership is engaged alongside technical staff to provide answers and interpretations.
The Cyber Heat Map assessment isn’t an exam or a compliance checklist where every blank counts against you. It’s an engine that generates a practical view of your cybersecurity posture quickly and determine where improvements are most needed.
Teams should provide the best-informed answers for each item without getting bogged down in debates over wording or nuance. There’s always room to refine responses later.
To get value from the platform, teams should initially focus on collecting baseline data quickly. The goal is to identify priorities so leadership can decide based on data, not to achieve a theoretical “perfect” score.
By avoiding these pitfalls, organizations ensure the Cyber Heat Map becomes an agile planning engine, not just another report gathering dust on the shelf.
The Cyber Heat Map framework prioritizes simplicity, actionable insights, and strategic decision-making. Many common security assessment methods bog teams down in extensive documentation, subjective scoring, and lengthy analysis. Too often, these approaches flip the 80/20 rule as teams spend 80% of their effort on low-impact documentation and only 20% on meaningful improvements. We designed Cyber Heat Map to avoid that trap.
Our approach uses simple questions to capture key data about your team’s skills, deployed technologies, and implementation status, rather than hundreds of granular control checks. This reduces assessment time and effort, freeing up resources to enhance and manage cybersecurity. The output isn’t a vague maturity description. It’s an intuitive set of scores (often on a familiar 0 to 100 scale) and color-coded charts anyone can understand. By simplifying both inputs and outputs, we keep the focus on what the data means and what steps you should take next rather than the assessment process itself.
Another key distinction is that compliance-driven methods can encourage a “check the box” mentality. Cyber Heat Map emphasizes building sustainable capabilities that fit your real-world constraints. We don’t ignore compliance, since we map all capabilities to standards as needed. However, the focus is on improving cybersecurity maturity, not just documenting compliance requirements. This provides immediate clarity, since a low score shows where you need to improve. Cyber Heat Map shows what you need to focus on improving rather than wondering what a level 2 versus level 3 maturity means in practice.
The framework offers practical benchmarking data from its growing user base. The platform anonymizes and aggregates all the data. As more organizations use the tool, you can see where you stand relative to peers (e.g., “schools of your size typically score 30 to 60 for this capability, and you’re at 20”). These comparisons help leaders communicate their cybersecurity posture in budget meetings or when talking with their boards. It’s powerful to show you’re lagging behind peers (justifying a budget increase) or that you’ve improved from a score of 20 to 50 in a year (demonstrating progress). Benchmarking turns subjective discussions into objective ones, making it easier to make informed decisions about investments and explain how previous projects have strengthened the program.
Adopting the Cyber Heat Map doesn’t mean abandoning established frameworks or duplicating work. The reporting engine maps to common standards, and the capabilities are cross-referenced to frameworks like NIST CSF, GLBA Red Flag Rules, and DoD CMMC guidelines. This means you can use Cyber Heat Map to drive internal strategy and still map your outcomes to external compliance or risk management frameworks you use. For example, if a control is required by NIST CSF, it’s already mapped to different capabilities and questions collected in Cyber Heat Map. The built-in mapping capability avoids redundant effort; a single Cyber Heat Map assessment can yield outputs for multiple reporting needs.
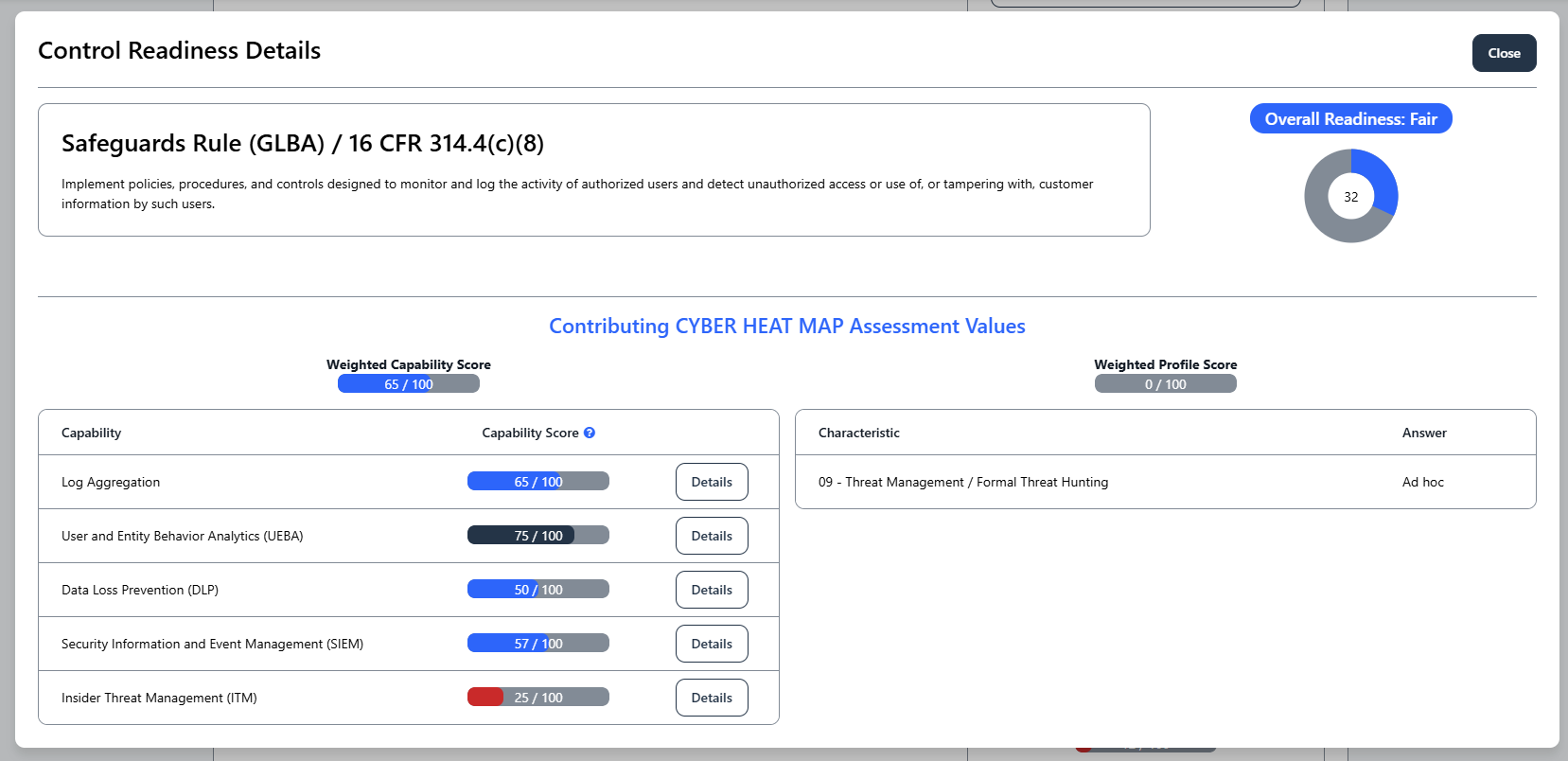
Cyber Heat Map complements other standards by providing a practical, organization-specific action plan. Users find it translates high-level requirements into concrete steps tailored to their environment, making compliance and certification audits more straightforward.
Cybersecurity is in constant flux. New threats emerge, technologies evolve, and today’s best practices may be outdated tomorrow. That’s why we designed the Cyber Heat Map framework as a dynamic planning engine, built to evolve alongside the threat landscape.
We monitor major cybersecurity research reports and shifts in vendor offerings to identify emerging capability areas. Then we gather direct feedback from our user community about new challenges they’re facing. Next, we assess whether we should add new security tools or approaches, like when Zero Trust grew from a buzzword to a formal strategy or when XDR (Extended Detection and Response) emerged as a mainstream solution. We then decide whether these represent distinct capabilities to add to the framework. If so, we integrate them and notify users about the updates and their significance. We also adjust the framework when technology convergence or vendor consolidation makes certain capabilities less relevant. We may merge or retire capabilities if they no longer provide distinct value. These updates occur multiple times a year, ensuring the framework’s taxonomy remains current.
Our goal is to spare users the hassle of reinventing their assessment every year. The platform automatically updates, requesting additional user input only when needed. Think of it as an app that we keep up to date; the content evolves, but we preserve your data and map it into the new structure. This ensures you always have a practical, current view of your cybersecurity posture without having to track every industry trend yourself. We handle that work for you behind the scenes.
Recognizing the overwhelming cybersecurity vendor landscape, we simplify hundreds of niche products into around 110 defined capabilities. This abstraction is crucial. For example, whether you use Vendor X’s VPN appliance or Vendor Y’s SASE solution, both might map to a capability like “Secure Remote Access.” By focusing on capabilities, Cyber Heat Map sidesteps marketing noise and shifting terminology. As the market consolidates or diversifies, we update those definitions in the background. (According to Gartner, 75% of organizations are actively seeking to consolidate vendors because of complexity. Our capability-centric view aligns perfectly, helping you identify overlaps and rationalize your solution stack.)
One principle guides Cyber Heat Map’s evolution: keeping it relevant and useful for decision-making. We don’t chase fads, but we don’t let the model stagnate either.
Cyber threats today differ from threats in 2015, and future years promise even more change. By continually improving the Cyber Heat Map models, we ensure your plans can adapt to the times. This prioritizes projects based on current and future needs.
Cybersecurity is a core business risk, but translating technical challenges into business terms can be difficult. Cyber Heat Map provides visualizations and simple scoring systems that help communicate ideas effectively, even to non-technical stakeholders.
Organizations have used these capabilities in several ways to improve communication:
These techniques have proven especially valuable for our early higher education users. Institutions have increased cybersecurity budgets by over 70% in the last five years, making it essential for IT leaders to communicate clearly how those investments have improved security posture. When a non-technical executive can see gaps and progress in a simple visual, it builds trust and confidence. The conversation shifts from technical warnings to strategic risk management with a data-backed plan. This is something any executive can appreciate.
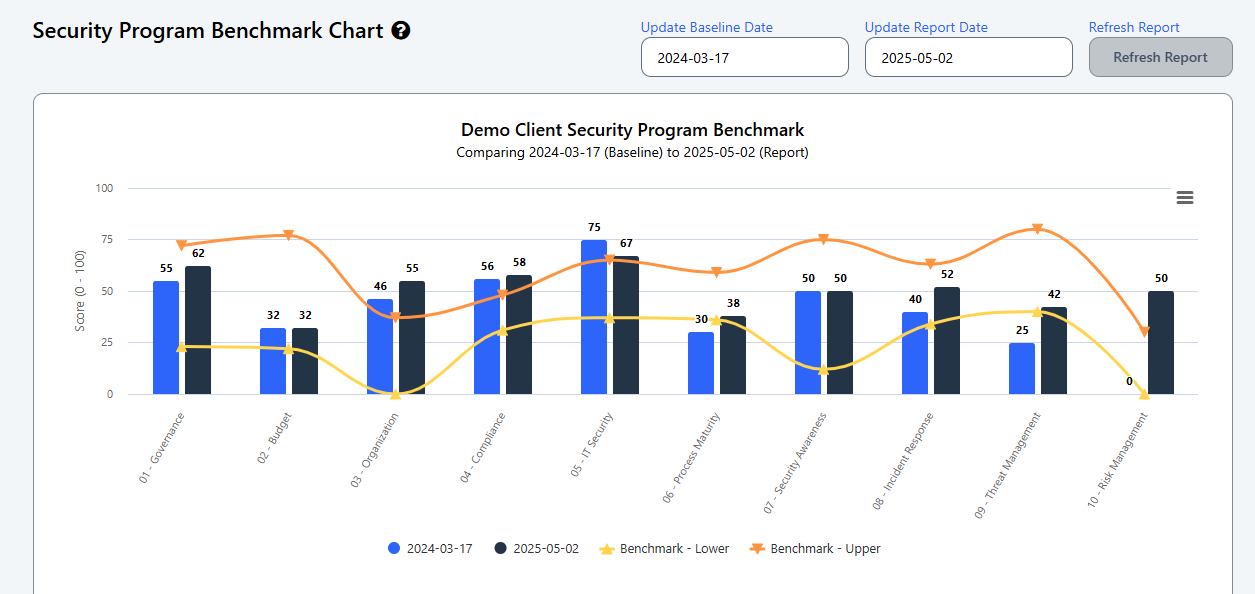
The Cyber Heat Map engine translates cybersecurity from technical jargon into business visuals. It helps CISOs and CIOs craft a strong narrative: current state, target state, and implementation plan. In an era where boards demand accountability and clarity on cyber matters, this bridge between technical detail and business objectives is invaluable.
The Cyber Heat Map framework streamlines cybersecurity planning and investment prioritization. Its “sand in a box” philosophy shows capabilities spreading horizontally across every domain before rising vertically into higher levels of maturity. That picture keeps teams focused on strong fundamentals first, producing a stable, effective security posture that squeezes maximum value from every dollar and hour.
For organizations with limited resources, from school districts and small municipalities to medium-sized companies, this method offers a realistic path to cyber resilience. Instead of chasing the latest tools or reacting to audit findings in isolation, Cyber Heat Map highlights what improvements enable everything else.
The most impactful gains rarely come from big-ticket products. Instead, they come from applying the unglamorous basics consistently. By linking those improvements to a data-driven roadmap, the platform helps leaders secure stakeholder support.
With clear visuals, holistic assessment methods, and practical prioritization strategies, Cyber Heat Map turns cybersecurity planning into a streamlined process. As threats evolve, this approach enables your program to evolve as well. Continuously updated planning guides help ensure cybersecurity investments deliver maximum value.
Cyber Heat Map guides technology leaders with tailored recommendations. This helps them build a robust security posture that meets the challenges of today and tomorrow, even with lean budgets and staffing levels.

Christian “Chris” Schreiber is a cybersecurity strategist and architect of the Strategic Operating System for higher education. He helps technology leaders cut through vendor noise and focus their limited resources where they matter most. He is the founder of CampusCISO® and the creator of Cyber Heat Map®, a cybersecurity planning platform used by 140+ technology and information security leaders. Chris previously served as a university CISO and held strategic roles in the private sector. Read more about Chris →
Complete Your Cybersecurity Assessment and Roadmap in Days
Join 30-Day Cyber Strategy Sprint for just $399
Build your own living roadmap in days, not months.
Includes a founder-led kickoff and 30-day access to the Cyber Heat Map® platform and weekly group guidance.
No sales pitch. No contract. Just results.
Secure Your Seat Now
$399 • Limited seats each week