
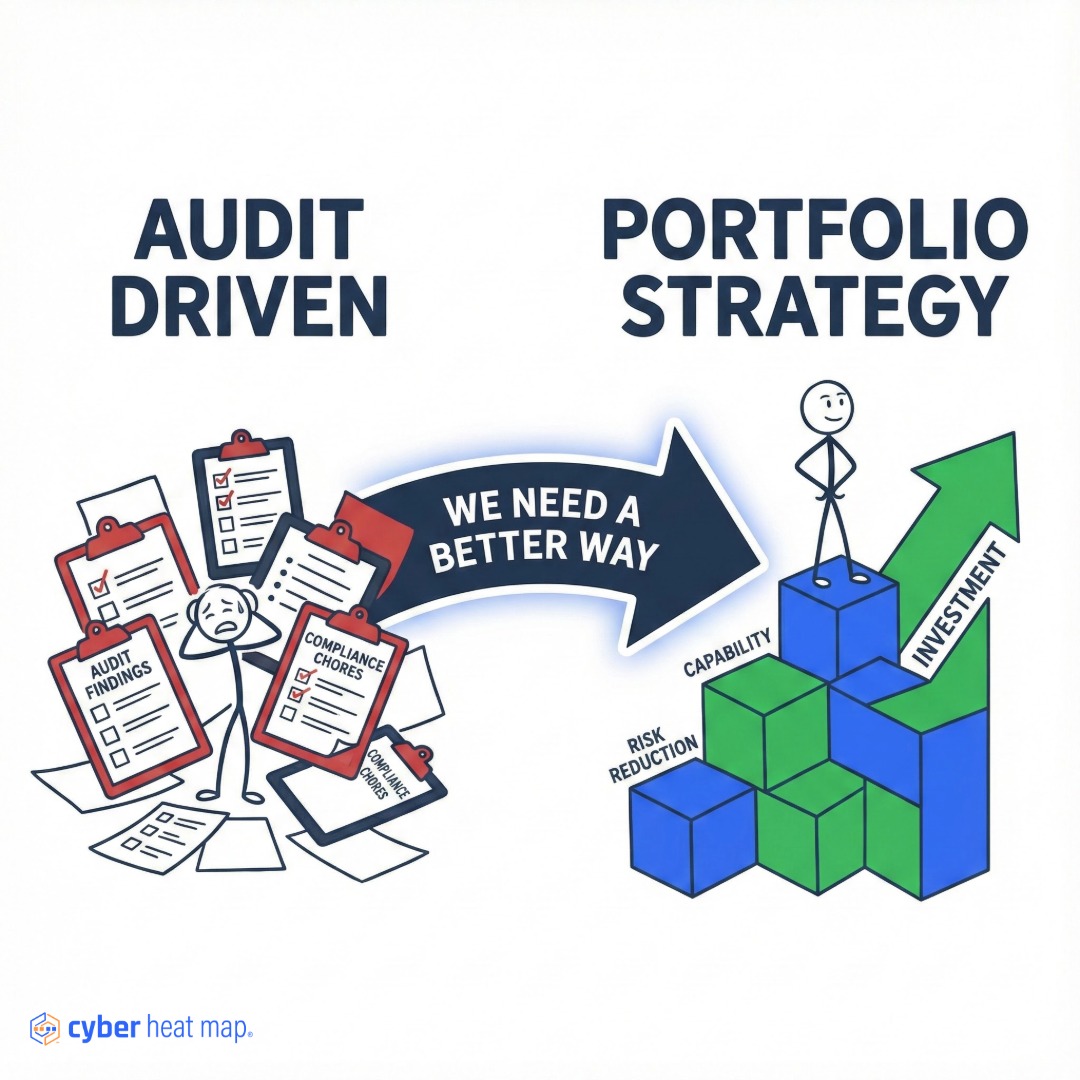
I wrote one line in my notebook that changed everything: “We need a better way.”
I wrote one line in my notebook that changed everything: “We need a better way.”
I had walked into an audit committee meeting ready to discuss risk, priorities, and a roadmap. We ended up debating password rotation and vulnerability scans, characterized as “closing audit findings 14, 15, and 16.”
The auditor, not my university’s leadership team, was setting security strategy.
In the same quarter, my team spent more hours on vendor questionnaires than on rolling out multi‑factor authentication. We were understaffed, underfunded, and drowning in paperwork while actual risks went unaddressed.
The compliance‑first mindset was crowding out practical risk reduction.
My background shaped how I saw the problem. I built a service where I had profit-and-loss responsibility at a Fortune 500 technology services company before becoming a university CISO. Owning outcomes, not just budget lines, taught me to treat security spending like any other investment.
What if we managed cybersecurity like a portfolio? Invest each dollar where it reduces the most risk, measure progress by capability coverage and outcomes rather than checklist completeness, and sequence improvements so each step amplifies the next.
That insight became the foundation for everything I teach today.
The auditor had focused on specific outcomes because the university’s policy required application‑level scans for every website. On paper, the control looked clean. In reality, we lacked a complete inventory, and the workload would have consumed my entire team for years. We looked into outsourcing the work, but the quotes were over ten times my entire security budget.
Instead, I chose a capability‑first path. We built a living asset inventory, deployed basic network telemetry to detect attack attempts, and created a registration policy requiring departments to scan before going live. Then, my team focused on scanning the highest-risk websites and performed periodic sampling elsewhere.
We framed this as risk‑based resource allocation. Leadership backed the plan, and board conversations shifted from “Did you scan everything?” to “Are we reducing risk, and how do we know?”
Compliance should follow capability, not dictate it.
When directors think in binary terms of “compliant or not,” I reframe compliance as one risk in the portfolio, not the finish line. I put two options side by side:
We score an Improvement Priority for each option (defined as expected risk reduction adjusted for relative cost and effort), then select the highest-yield moves. We also note where the work maps to familiar frameworks, like NIST CSF or GLBA, without letting a framework checklist dictate the overall strategy.
As board members get used to seeing security investments in portfolio terms, the concept sticks. Strategy comes first, capabilities are the engine, and compliance is the odometer that reflects how well the program runs.
After guiding 140+ leaders, I’ve realized the most common barrier is perfectionism. Leaders want certainty before committing dollars, which delays progress.
Despite increasing cybersecurity budgets, 28% of CISOs report dissatisfaction with their budget allocations. Often, the problem isn’t funding. It’s how you divide funds among competing needs.
To fix this, you can adopt a simple operating rhythm.
Once you establish this framework, keep a steady cadence for updates and reporting progress. Provide a one-page snapshot of your capabilities, a Top 5 list of your next projects, and rebalance every 90 days so progress is transparent and defensible.
This produces visible momentum and a defensible story that you can share with executives and auditors.
The transformation requires treating cybersecurity as part of the enterprise investment portfolio, not as a standalone cost center.
Your risk surface spans identity, networks, data, and applications. Many of those budgets sit outside the security team. If each group optimizes in isolation, you over-fund some controls, under-fund others, and still miss material risk.
Create a single capability view across IT and security. Force every proposal onto one list with three fields: expected risk reduction per dollar, dependencies, and operational impact.
Rank everything as a portfolio.
If identity governance is weak, replacing a firewall may not move the needle. If disaster recovery is shaky, new log analytics tools will not save you when data breaches average $4.88 million in costs.
Your goal should balance allocations that close foundational gaps, amplify existing investments, and sequence projects so each step lifts the next.
Security planning is an investment discipline, not a compliance chore.
Treat your program like a portfolio: every dollar has a job, tradeoffs are explicit, and progress is measured by overall capability coverage, not by the length of a checklist.
Stop waiting for the perfect answer. Start investing in the best next moves.
Your program, your people, and your board will reward visible risk reduction delivered on a predictable rhythm.
That frustrated CISO writing “We need a better way” in his notebook discovered something powerful: progress beats perfection every time.

Christian “Chris” Schreiber is a cybersecurity strategist and architect of the Strategic Operating System for higher education. He helps technology leaders cut through vendor noise and focus their limited resources where they matter most. He is the founder of CampusCISO® and the creator of Cyber Heat Map®, a cybersecurity planning platform used by 140+ technology and information security leaders. Chris previously served as a university CISO and held strategic roles in the private sector. Read more about Chris →
Complete Your Cybersecurity Assessment and Roadmap in Days
Join 30-Day Cyber Strategy Sprint for just $399
Build your own living roadmap in days, not months.
Includes a founder-led kickoff and 30-day access to the Cyber Heat Map® platform and weekly group guidance.
No sales pitch. No contract. Just results.
Secure Your Seat Now
$399 • Limited seats each week