
Cyber Heat Map turns tight budgets into solid cyber defenses. The “sand in a box” model spots gaps, helps reduce shelfware, and creates data-driven roadmaps ready for board and executive approvals.
Your attack surface keeps growing while your budget remains flat. Sophisticated threats multiply daily, yet your board expects airtight defenses without offering additional dollars. Sound familiar?
This tension creates an impossible equation: do more with less while justifying every dollar spent on cybersecurity. The traditional approach of chasing new tools and reacting to the latest threats simply doesn’t work anymore.
But there’s a better way.
Organizations still treat cybersecurity as a checklist: close the audit finding, buy the recommended tool, move to the next gap. The result? A patchwork of projects that chase compliance rather than build sustained resilience.
A capability-first approach flips that logic.
Instead of asking “Which product fixes this finding?” ask “Which core security capabilities must exist at the right maturity to reduce risk across the board?”
This shift transforms cybersecurity from an arms race into a resource allocation puzzle. Your goal isn’t accumulating the most tools. It’s strategically deploying limited resources where they deliver maximum risk reduction.
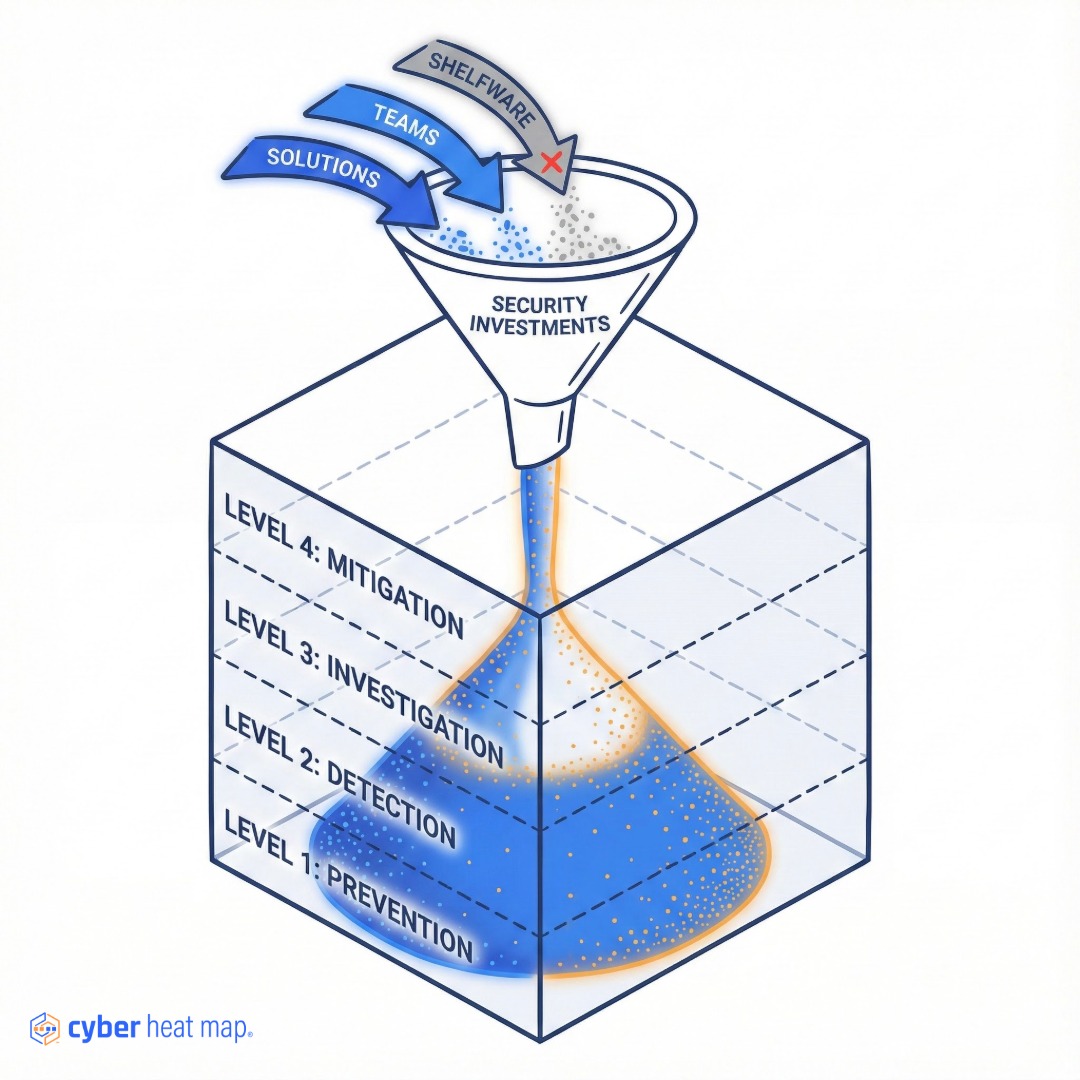
Picture an empty wooden sandbox. When you pour sand, it always spreads until the sand covers the base. Only then does it rise in tidy mounds.
Cybersecurity maturity works the same way.
Foundational controls like asset inventory, multifactor authentication, secure backup, and log collection form your base layer. If you try to pour advanced tools like AI-powered analytics onto an uneven surface, the capabilities slip into the gaps. You pay for features you cannot fully leverage.
The “sand in a box” metaphor turns physics into practical budgeting strategy. First, level the sand by funding minimum-viable capabilities across every technical category. Once coverage is uniform, each additional dollar lifts your entire security posture instead of creating isolated towers of excellence.
Industry studies consistently show that organizations only use about one-third of purchased software features. Flexera’s SaaS-management analysis puts average under- or unused licenses at approximately 30 percent of spend, with some environments climbing past 40 percent.
Security tools are no exception. Redundant endpoint agents, dormant SIEM modules, and half-configured cloud security add-ons quietly renew year after year, consuming precious budget while foundational controls remain under-funded.
These hidden costs accumulate on several fronts:
The first step toward better resource allocation is understanding what you already own and what’s actually being used.
Let’s see how this approach works in practice.
A mid-sized community college ran a capability assessment using Cyber Heat Map. The dashboard immediately surfaced two critical insights:
First, several baseline capabilities—backups, MFA coverage, and centralized logging—scored in the low-40s on a 0-100 maturity scale, well below peer benchmarks.
Second, the institution had redundant endpoint security and legacy log-management licenses, consuming nearly 15 percent of the annual security budget.
Armed with a data-ranked improvement list, the CIO drafted a phased roadmap instead of requesting a “big-bang” spend. Year one focused on leveling the sand: reallocating dollars from redundant contracts, adopting campus-wide MFA, and automating off-site backups.
Because each action closed multiple capability gaps, the college raised every foundational domain above the peer median without requesting extra funds.
The maturity report, with its simple 0-100 scoring, gave the board proof of progress. Seeing that momentum, leadership approved a modest net-new investment in a lightweight SIEM that addressed the next cluster of high-impact gaps.
Today, the college uses quarterly check-ins with a cross-functional steering committee of executives to keep its cybersecurity roadmap relevant. This ensures new purchases build upward only after the base remains level.
When a capability assessment shows that most of peer organizations already run multifactor authentication or centralized backups, directors instantly understand why “doing nothing” is no longer defensible.
Boards want this kind of comparison data. 93 percent now view cyber-risk as a direct threat to stakeholder value, but just 23 percent feel their current metrics give them the visibility they need.
Benchmarks close that visibility gap in three ways:
Peer data replaces gut feel with credible context, helping executives allocate scarce funds where they deliver the biggest maturity lift.
Ready to improve your security posture without new funding? Start with these five steps:
Run a comprehensive capability assessment. Teams complete an assessment in just a few hours. You’ll get a 0-100 maturity score for approximately 100 capabilities, peer benchmarks, and a ranked gap list.
This data replaces weeks of spreadsheet audits and gives leadership a single source of truth.
Cross-check top-ranked gaps against tools you already license. Many identity platforms include MFA, and most endpoint agents ship with EDR modules that are never activated.
According to Gartner, nearly half of installed software features go unused. Use what you have before buying anything else.
Prioritize fixes that reduce the largest attack surface for the least effort:
If your assessment flags overlapping licenses, schedule those renewals for termination and redirect the savings to high-impact gaps.
Publish a one-page roadmap, assign owners and 90-day targets, and revisit the dashboard quarterly. Executives see measurable progress; practitioners gain a living plan instead of another static audit.
All without requesting extra budget.
The resource-allocation mindset elevates board dialogue from “headline risk” to measured ROI. Instead of leading with vendor slogans or worst-case breach stories, CISOs can show a one-page heat map that ties every dollar to a measurable capability score and a peer benchmark.
When directors see that just 35 percent of CISOs feel their boards fund cybersecurity adequately, according to National University, they ask, “Where are we on that curve, and what would it cost to close the delta?”
Cyber Heat Map assessments usually identify unused features, allowing leaders to reallocate funds instead of approving net-new line items.
Because each recommended project includes a projected maturity lift, boards can debate trade-offs with the same discipline they apply to capital planning: “Will this $40K raise three critical capabilities by ten points, or should we divert it to MFA coverage?”
The conversation shifts from fear, uncertainty, and doubt to quantifiable progress, giving executives confidence that limited resources are being deployed where they reduce enterprise risk the most.
Cyber Heat Map turns a few hours of data entry into a board-ready action plan through a six-step process:
Because everything lives online, teams update data as they deploy or retire tools, letting the roadmap grow from a static audit to a living, data-driven planning guide.
Cyber Heat Map turns cybersecurity planning into a shared, data-driven exercise rather than a turf war. Because the platform inventories every capability—whether it lives with the network, email, infrastructure, or desktop team—each group sees its own work reflected in the same 0-100 maturity scorecard.
This transparency levels the playing field. Decisions pivot on measurable gaps and available skills, not historical budget size or the loudest voice in the room.
When the roadmap shows that enabling MFA lifts four capabilities while a new analytics tool lifts just one, consensus forms around the higher-impact option regardless of who “owns” it.
Role-based access lets stakeholders update their own sections, so the CISO is no longer the sole messenger. Network engineers document firewall progress, infrastructure staff track backup improvements, and the collective dashboard updates in real time.
The result is a holistic, continuously updated plan that boards view as responsible stewardship, security teams view as fair, and budget owners view as maximized ROI—all without hiring consultants to rewrite the strategy every year.
Your cybersecurity needs continually shift, with threats growing more sophisticated and attack surfaces expanding. But your budget likely isn’t keeping pace.
By shifting from an arms race mentality to a resource allocation mindset, you can make every dollar count. Focus on building a solid foundation across all capability domains before investing in advanced tools. Use data-driven assessment to identify and prioritize gaps. Leverage peer benchmarks to build consensus and earn leadership buy-in.
Most importantly, remember that effective cybersecurity isn’t about having the most tools. It’s about having the right capabilities at the right maturity levels to protect your most critical assets.
Start by understanding what you already have. Activate unused features. Eliminate redundancy. Build from the foundation up.
Your limited resources can still deliver powerful protection when allocated strategically.
Ready to see how your security roadmap stacks up? Take the interactive product tour.

Christian “Chris” Schreiber is a cybersecurity strategist and architect of the Strategic Operating System for higher education. He helps technology leaders cut through vendor noise and focus their limited resources where they matter most. He is the founder of CampusCISO® and the creator of Cyber Heat Map®, a cybersecurity planning platform used by 140+ technology and information security leaders. Chris previously served as a university CISO and held strategic roles in the private sector. Read more about Chris →
Complete Your Cybersecurity Assessment and Roadmap in Days
Join 30-Day Cyber Strategy Sprint for just $399
Build your own living roadmap in days, not months.
Includes a founder-led kickoff and 30-day access to the Cyber Heat Map® platform and weekly group guidance.
No sales pitch. No contract. Just results.
Secure Your Seat Now
$399 • Limited seats each week